After struggling for decades pursuing bank robberies and credit card fraud, criminals have really found their footing in crypto. Since 2016, cybercriminals have pilfered a colossal $7 billion from crypto companies and DeFi protocols.
Of this amount, almost half is attributed to one organisation: the North Korean state-sponsored Lazarus Group. And according to cybersecurity experts, much of the profit from the group’s crypto heists is funnelled into the hermit kingdom’s nuclear weapons programme.
But Lazarus is not alone. There are many more cybercrime groups and opportunistic hackers that use a variety of hacks and exploits to take users’ hard-earned crypto.
While the terms hacks and exploits are often used interchangeably, they have slightly different meanings.
Hacks refer to someone gaining unauthorised access to data, while exploits involve manipulating code bugs or loopholes to gain an advantage within a system — usually with the goal of extracting sensitive data, money or crypto.
Let’s take a look at some different kinds of hacks and exploits, how they work, and how you can track the damage they cause on DefiLlama.
Hacks
A hack is a broad term applied any time someone gains unauthorised access to data in a system or computer.
This can take many forms: a hacker can infiltrate a computer network by planting malicious code directly into a system, or by convincing someone to open a dodgy file that, when clicked on, allows the hacker to swipe their data.
Below are some of the most common kinds of hacks in crypto:
Malware hacks
Malware hacks are where someone uses a file or code that infects, explores, steals, or conducts some behaviour an attacker wants. In crypto, the goal of those distributing malware is often to steal the password-like private keys that grant access to crypto wallets.
As we’ll see, malware is a key component of other kinds of hacks, such as phishing or ransomware.
Ransomware
Ransomware is a type of malware which prevents a user from accessing their device and the data stored on it, usually by encrypting their files.
The ransomware software demands the user send cryptocurrency to the hacker to remove the encryption and let them access their files.
The May 2021 Colonial Pipeline attack is one of the most high-profile ransomware cases in recent years. Hackers hit the Colonial oil pipeline with ransomware, resulting in a shutdown of operations, and demanded a 75 Bitcoin ransom, worth about $4.4 million at the time.
The pipeline’s operators paid the ransom, and were able to restart operations. But less than a month later, the US Justice Department announced it had found and recaptured the majority of the ransom, and attributed the hack to DarkSide, a Russian hacking group.
Frontend hacks
Frontend hacks are where hackers break into the websites that let users interact with DeFi protocols or other crypto services and manipulate the site’s code for nefarious purposes.
In 2021, users of the DeFi protocol BadgerDAO suffered $120 million in losses after hackers targeted the protocol’s website.
The hackers injected malicious code into the BadgerDAO website letting them generate rogue transaction approvals.
To users, these transactions looked normal. But when approved, they allowed the hackers to pull funds into their own wallets instead of those controlled by BadgerDAO.
Phishing
Phishing is the practice of sending fraudulent emails or other messages purporting to be from reputable companies in order to induce individuals to reveal personal information.
The main target of phishing attacks are the password-like private keys that grant access to crypto wallets. One of the most common phishing techniques involves disguising malicious software within computer files, such as email attachments.
In crypto, phishing attacks are everywhere, and they can be highly lucrative if executed correctly. Lazarus Group has been one of the most successful phishers, draining over $700 million worth of crypto via phishing in 2022 alone.
In one of its more recent heists, Lazarus used a bogus job offer to an unassuming employee at crypto payments provider CoinsPaid to steal $37 million. The employee, under the impression they were being interviewed for a lucrative job with centralised crypto exchange Crypto.com, downloaded malicious software as part of a supposed technical test.
When the employee downloaded the malicious file, it gave hackers access to CoinsPaid’s system, where they were then able to exploit a software vulnerability to withdraw funds from CoinsPaid’s crypto wallets.
Cryptojacking
Cryptojacking is a type of malware attack specific to crypto.
Hackers secretly install crypto mining software on their victims’ computers, often through infected files. Using the victims’ computing power, the software mines cryptocurrencies on behalf of the attacker.
The sources of computing power can be startlingly large. Russian scientists secretly cryptojacked their own nuclear facility supercomputer to mine Bitcoin in 2018, before they were found out and arrested.
And in February that year, a security researcher found cryptojacking code within the homicide page of the Los Angeles Times.
SIM swapping
SIM swapping is when hackers gain control of a victim’s SIM — or cell phone number and accompanying information — with the goal of hacking accounts tied to it.
Hackers usually gain control of numbers in a surprisingly direct manner. They call up the mobile phone carrier pretending to be the owner of the SIM, and then use social engineering techniques to convince the operator to give them control.
Once a hacker gets the number transferred to them, they can use it to receive codes for the victim’s two-factor authentication via text. These can help the hacker gain access to the victim’s accounts on centralised exchanges and transfer their crypto assets out of them.
On December 1, 2022, a Florida man was sentenced to 18 months in prison after stealing over $20 million worth of crypto in a SIM swap attack.
Bonus — Confidence scams
While not a hack in the traditional sense, confidence scams are when a scammer uses psychological manipulation and social engineering techniques to establish credibility and create a sense of urgency or opportunity, with the end goal of stealing a victim’s money or crypto.
Whether they take the form of fake celebrity endorsements, the promise of easy money, or romantic companionship, these scams prey on the victim’s fears, desires, and vulnerabilities.
So-called Pig Butchering scams are a type of confidence scam that have made frequent headlines in recent months. They involve a hacker building rapport and trust with the victim, often by helping them make money through crypto trading.
This is crudely painted as fattening the victim up, before the trust the hacker has garnered allows them to dupe the victim out of all their money — i.e. butchering them like a pig.
Exploits
Exploits are different from hacks in that they involve directly manipulating existing code to gain an advantage within a system.
In crypto, exploits are usually performed to extract money or valuable crypto assets. This often involves finding bugs — or unintended loopholes — in smart contract code that allow the hacker to transfer funds from a DeFi protocol or its users to the exploiter’s crypto wallet.
With fresh smart contracts going live on blockchains like Ethereum every day, there’s plenty of opportunities for a bug to slip by developers.
Let’s take a quick tour of the most common kinds of crypto exploits:
Oracle manipulation
Oracle manipulation is where an exploiter causes an oracle to report inaccurate or stale information — usually about the prices of crypto assets.
Oracles are foundational to DeFi. They bring data, such as crypto asset prices, from off-chain sources and put it on the blockchain for smart contracts to use.
Bad actors can manipulate oracles using large amounts of crypto. They target low-liquidity tokens and quickly increase trading volume to pump up the price of the asset on a specific DeFi protocol.
Because it’s done so quickly, that price increase isn’t immediately reflected in the wider market. This lets the exploiter exchange their artificially inflated holdings for other tokens with a more consistent value, or use them as worthless collateral to take out loans, without the intention of ever repaying them.
Avraham Eisenberg’s 2022 Mango Markets exploit is a famous case of price oracle manipulation.
Integer overflow
Integer overflow is a quirk of how computers process data that can have some pretty big consequences.
If a user inputs a number into some code that’s larger than it can handle, it can sometimes roll over the number to the lowest possible value.
For example, if something were coded to have a maximum value of 255, increasing the value from 255 by one could roll it back to 0.
In the context of smart contracts that govern millions of dollars in DeFi, integer overflow can have disastrous consequences if not properly managed.
In 2018, an integer overflow attack on an Ethereum token called Beauty Chain allowed an exploiter to create an absurd amount of the token, instantly killing the project.
Although integer overflow bugs in Ethereum have since been patched, the possibility for new ones to pop up elsewhere in the crypto industry remains.
Reentrancy attacks
Reentrancy attacks are a way for an exploiter to repeat an allowed interaction with a smart contract more times than they should be able to.
Because Ethereum doesn’t synchronise states between smart contract interactions, exploiters can potentially repeat the same interaction if they can reenter the smart contract before the state is updated.
This lets them execute actions repeatedly which were only intended to be executed once — such as withdrawing a specific amount of tokens from a contract.
By repeating token withdrawals through reentrancy, an exploiter can forcefully drain all the tokens held in a specific smart contract.
The 2016 DAO hack, a notorious example of a reentrancy attack, led to the loss of around 3.6 million Ether, valued at approximately $50 million to $60 million at the time.
Despite being used in one of crypto’s highest profile exploits, reentrancy attacks still remain one of the most common exploits.
Bonus — Flash loans
Flash loans are uncollateralised DeFi loans that must be paid back in the same Ethereum block they were taken out in.
They are usually used to keep DeFi markets efficient by helping with arbitrage, liquidations, and collateral swaps. But they also make possible exploits which involve leveraging large amounts of tokens.
As such, flash loans make an appearance in 11% of all recorded crypto thefts, according to DefiLlama data.
A recent exploit that used flash loans was the Euler Finance attack in March. Thankfully, the attacker later returned all the stolen funds after complaining of a guilty conscience.
DefiLlama’s Hacks dashboard
DefiLlama’s Hacks dashboard keeps track of the shady underworld of crypto. Don’t be fooled by the name — the dashboard tracks scams and exploits, too.
Recorded events date back to the 2016 Ethereum DAO hack, when an attacker drained the first deployed smart contract of $60 million worth of Ether.
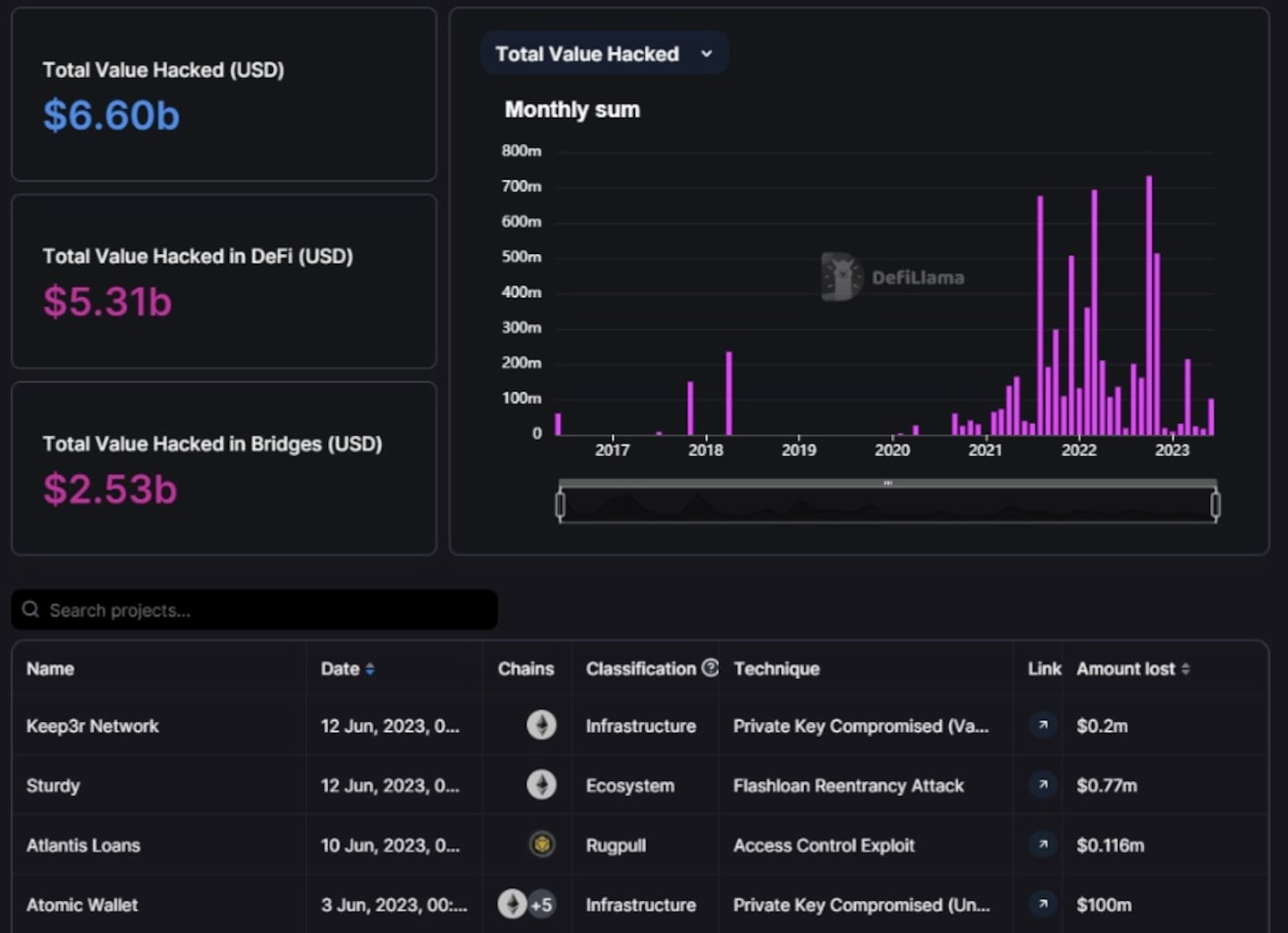
The dashboard displays the date of each attack, along with the protocol and blockchain where it occurred, the type of hack or exploit employed, and the amount lost.
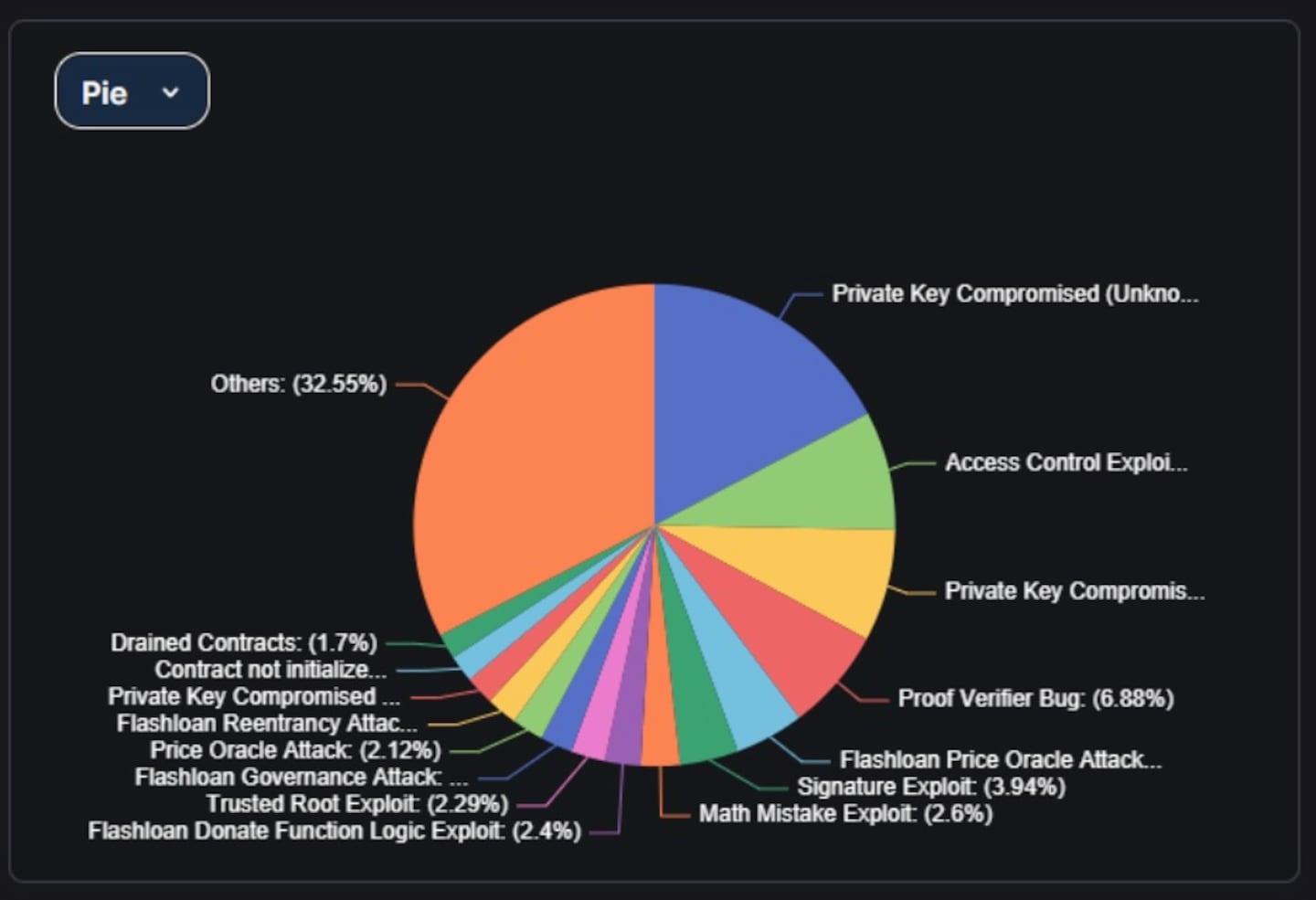
As the pie chart above shows, compromised private keys account for over 25% of cryptocurrency thefts.
These thefts involve four of the ten largest crypto heists recorded by DefiLlama. Thieves often steal private keys using social engineering, phishing, and malware attacks.
Some private key thefts have even turned out to be inside jobs conducted by rogue employees.
Bridges, the infrastructure that lets crypto users move funds between blockchains, have suffered greatly from compromised private keys.
So much so that DefiLlama calculates a Total Value Hacked in Bridges metric, which currently accounts for more than one-third of crypto lost in hacks.
For example, the Poly Network bridge has suffered several hacks, with the latest occurring in July, when a hacker compromised three out of four private keys used to control the bridge.
This allowed the hacker to mint a nearly unlimited amount of placeholder bridge tokens and use them to swipe $10 million.
Other bridges looted due to lax private key security include the Ronin, Harmony, and Multichain bridges.
As should be clear by now, the crypto market is fraught with risks, and even the most seasoned investors can still fall prey to hacks and exploits.
DefiLlama cannot stress enough the importance of safely securing your private keys, passwords, and cellphones.
Take proactive measures to safeguard your assets and identity — including never using the same password across multiple sites, and avoiding downloading email attachments and files, even from trusted sources.
And if something sounds too good to be true, RUN!
Next steps
- Read the Gate.io court documents detailing the first legislated instance of compromised private keys in cryptocurrency history.
- Weigh in on the “Code is Law” debate by reading up on the Indexed Finance attacker.
- Learn about Compound’s $147 million math mistake.


